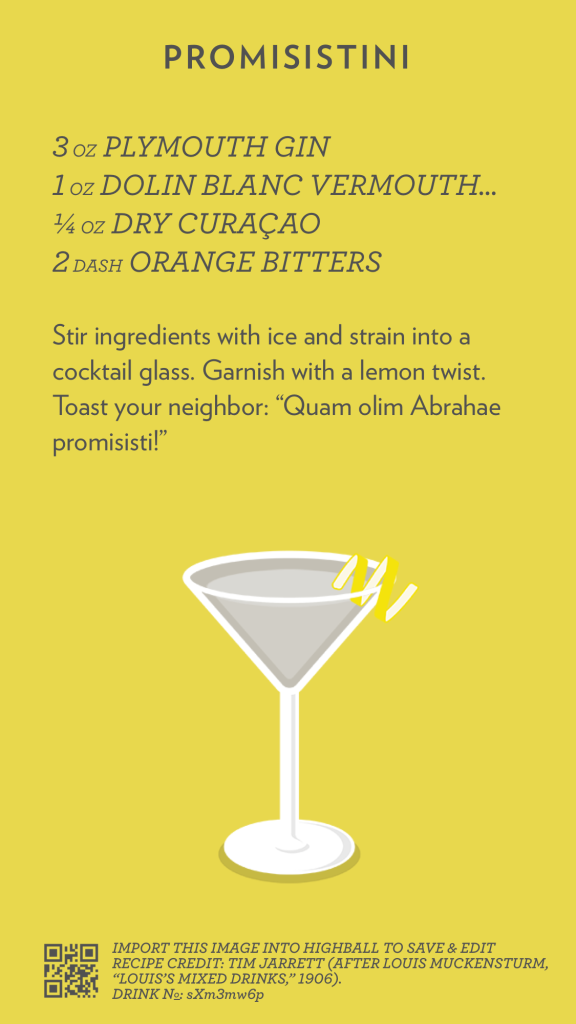
Album of the Week, May 10, 2025
Some young artists get their start playing with other young artists, and their eventual first record captures them coming up together as a unit. That’s usually the way it goes with rock and pop artists; jazz has often been another story. The first recordings of artists like Herbie Hancock, Wayne Shorter and others put the young lions in combination with older, more experienced players. You can especially see this on Blue Note Records. Alfred Lion’s trick accomplished a few things: it provided the young player with backup from players who had more experience recording and playing, who could challenge them improvisationally; but it also ensured that there was a certain continuity of sound between the new player’s album and the others on the label—or more generally in that generation of sound.
I don’t know if the Blue Note model was on the mind of Delfeayo Marsalis, who produced Marcus Roberts’ debut session as a leader, The Truth is Spoken Here. But the band assembled for the session followed the model, combining some new players with the proponents of the “house sound”—the Wynton Marsalis combo—and a few veterans. Alongside Roberts were his erstwhile bandleader Wynton (on three tracks), bassist Reginald Veal and tenor saxophonist Todd Williams (on two tracks) who were both to begin performing with Wynton’s band, Charlie Rouse (appearing on three tracks, best known for his long collaboration with Thelonious Monk), and Elvin Jones, who had spent the years since his collaborations with John Coltrane leading his own combos. The choice of veterans must have been a deliberate choice; Roberts wore his indebtedness to Monk on his sleeve, and the influence of Trane’s pianist McCoy Tyner cast a long shadow over his playing as well.
The first track, “The Arrival,” demands close listening to get the exciting bits; I recommend headphones because Jones is an extremely vocal player, and hearing his grunts as the band plays through Roberts’ composition makes it come alive in a way that the playing (sadly) doesn’t. We’re hearing Wynton in his Miles phase, playing through a Harman mute, and while the tone is impeccable the whole solo feels like it happens all on one level, with little variation in intensity. Roberts gives the other players a lot of space, primarily letting Wynton, Elvin, and Reginald Veal drive the development of the track during Wynton’s solo. Veal is eye-opening here; his bass lines are acrobatic, but he’s not content just to walk them; we get rhythmic variation and counter-melody from him as well as some suspensions that build tension. When Roberts takes his own solo we start to hear a little more flash. There’s some stride in his playing in the way the left hand shifts the beat, and some Liszt around the edges of his chord voicings. You can hear the debt to Tyner in the harmonic vocabulary, but the touch (particularly when Wynton plays) is lighter. The outro for Elvin Jones is a shot of adrenaline even without the great drummer’s grunts signaling the beats.
If the opening showed what Roberts could do in a group context, “Blue Monk” is pure solo, and offers him the chance to really show off. He takes the Monk standard to church: while the opening is pure Monk, once he gets past the head we get some gospel around the edges, and more than a hint of the blues and ragtime that are always just under the corners of any Monk composition—especially what those left hand chords do to the time as he shifts freely from 4/4 to 6/4. It’s way more interesting than what he played on the first track; one wants more of it.
“Maurella” is another Roberts original, and it has the marks of the compositional direction he brought to his time in the Wynton Marsalis group on albums like J Mood: a series of suspended chords, taken so slowly in the head that it almost feels out of time, that ultimately fail to resolve. Roberts loved these chord suspensions so much that you can hear traces of them in other tracks, including the title track on the second side. In this setting, the progression seems to open up melancholy vistas behind the melodic trail blazed by Todd Williams, a tenor player from St. Louis who would spend about ten years in Wynton’s band and related projects before withdrawing from jazz performance to take the music director role at the Times Square Church. His tone is well suited for this work; he sells the odd chord progressions but doesn’t do much showy improvisation. There’s sensitive accompaniment from Jones and Veal throughout.
“Single Petal of a Rose” is the second solo number by Roberts, this time paying homage to Duke Ellington and Billy Strayhorn. He plays the Strayhorn composition with delicacy and nuance, but with a power in the left hand that gives the work a deep dynamic range. When he gets to the bridge, you can almost get swept away on the wave of impassioned music making that pours out of the piano. Like “Blue Monk,” this one also leaves you wanting more of his solo work.
When we flip to the second side, we have shifted gears again and are in a straight-ahead post-bop number. “Country by Choice” features Charlie Rouse. Rouse played as Monk’s sideman from 1959 through 1969, including on some of the most famous Columbia Records recordings (Criss Cross, Monk’s Dream, It’s Monk’s Time, Straight, No Chaser). Here on more straightforward harmonic material he tempers some of his more eccentric harmonic tendencies, but he still brings a big tenor sound to the party. Roberts’ solo feels a little tentative through bits of the middle; he’s on firmer ground when he shifts the meter to something more syncopated and shouting, and Veal and Jones follow him the whole way. We get a shouting, snarling solo from Jones to bring us through into the recap, and Veal and Jones bring us out into a coda.
“The Truth is Spoken Here” brings the chord progressions first heard on “Maurella” to a quintet voicing with the addition of Wynton’s trumpet. Wynton takes a good deal more rubato than was present in the earlier iteration of the tune, and plays off Todd Williams’ high tenor notes with aplomb. This time Roberts takes the first solo, and his anticipatory downbeats combined with Jones’ growl lighten up the proceedings considerably compared to the earlier song. The trio cooks its way through the end of the solo and into the reprise. It’s a great performance, lessened only by the puzzling near-repetition on the first side of the record.
“In a Mellow Tone” brings back Rouse for a seriously swinging run at the Ellington classic, and the combination of Rouse’s tenor and Jones’ vocalizing recall nothing so much as the collaboration between Ellington and Coleman Hawkins that produced “Limbo Jazz” (particularly the echo of Aaron Bell’s spontaneous vocals on the latter tune). Veal stays particularly tight in the pocket, letting Roberts unspool melodic lines and shifts of rhythmic emphasis against an always-solid metrical backbone.
“Nothin’ but the Blues” gives us a staggering blues, with a tricky triple meter laid over the traditional twelve bar form. This track is the only time that I’m aware that Rouse and Wynton collaborated (Rouse would pass away only five months after this session, his last, was completed), and their off-kilter harmonic imaginations light up sparks on the head. Roberts may have called this “nothing but the blues,” but there’s more than a little Monk in it too, particularly in his solo, which gets more interestingly ornery the longer it goes. Wynton’s solo straightens out some of the brilliant corners, but it’s a more committed improvisational gesture than on the rest of the record, and it pairs well with Rouse’s sly around-the-corner elaboration of the chords. The outro gives each of the players a plausible claim to having gotten the last word.

As a debut album, The Truth is Spoken Here does a good job of showcasing Roberts as a performer, particularly in the two solo numbers and “In a Mellow Tone.” It’s less good at showcasing his compositional skills, but does a great job of highlighting his influences and demonstrating how his gospel, soul and classical background helped his perfoming conception transcend those influences. Like a good Blue Note album, the end result is a great listen, if not groundbreaking. As for his composition, the follow-up album would show a much broader range of his talents. We’ll hear that one in a bit; next time we’ll hear a different musician tackle traditional repertoire alongside a storied collaborator.
You can listen to this week’s album here:
BONUS: With Wynton guesting on the album and given their close working relationship in his small group, it was only natural that some of Roberts’ originals would end up on a Wynton album. The title track appeared on Wynton’s 1991 album Uptown Ruler in a quintet performance: